So I guess you have all read Dan's post (and seen Sarah's video, of course :-).
... And I guess many of you have used the DNS checker on doxpara.com to see if your DNS is vulnerable (although, personally, I like the "dig +short porttest.dns-oarc.net TXT" method better). Well, so did I (and neither my home provider, my mobile provider nor $CUSTOMER have fixed their DNS yet) and of course using wasn't enough, I had to look more closely at how it works ...
Turns out it is doing a simple lookup on $randomstring.toorrr.com, which resolves to the webserver via a CNAME chain that encodes the interesting data from the queries that are sent out by the resolver. So what does Dan do with it then? He writes a file with the query details (requested hostname, date, source ports and query IDs) to /fprint/$randomstring on his webserver (which is automatically deleted after about two minutes or so), which the script then fetches using some AJAX-magic. Luckily for me, he forgot to turn of the directory listing on /fprint/, so not only the original requestor could download the result files, but me too.
Thus, for the last few days, I have been doing something along the lines of while true; do rm 209.200.168.66/fprint/index.html; wget -U "Hi Dan, just compiling some stats, hope you don't mind ... Alex" -r -nc -l inf http://209.200.168.66/fprint/; sleep 30; done and put the output into a database. 471690 queries later, Dan apparently noticed and put a »*laughs*« into /fprint/index.html.
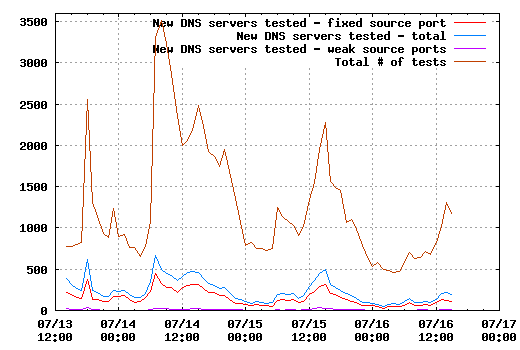
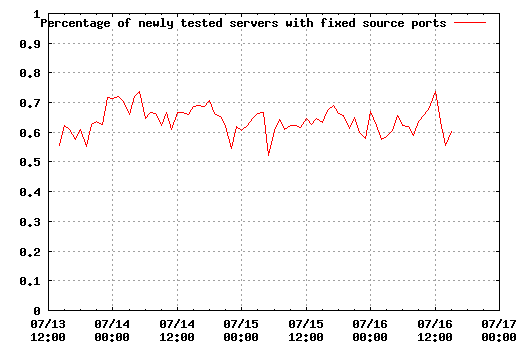
Well, still enough data to produce some interesting graphs. The first one shows the number of new IPs appearing every hour and how many of those had fixed source ports and weak source ports (max(srcport) - min(srcport) < 100).From here, one can already see that the red line (fixed source ports, thus apparently vulnerable to what Dan's been cooking up) is still more than 50% of the blue one - here are the percentages of red vs. blue:
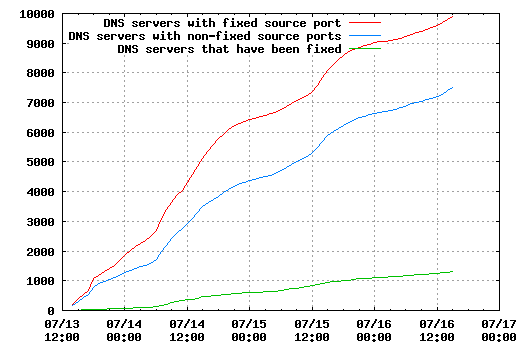
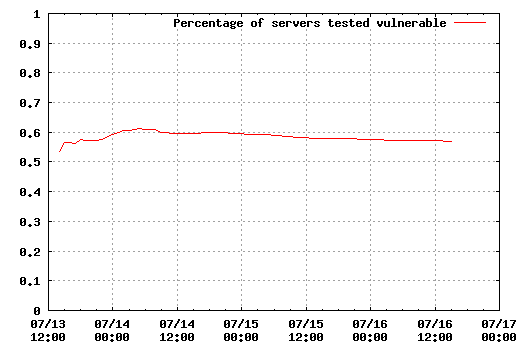
But of course, it is not only interesting how many new vulnerable servers are discovered, but what happens to the old ones. The next two graphs show the number of vulnerable servers at the time (some of those may have been fixed, but not retested afterwards, so take the figures with a grain of salt) and how many have been fixed.
Let's hope that the numbers change a bit before August 6th or I guess all hell will break loose ...